Unraveling the Digital Maze: Business Intelligence Tools for Threat Analytics
In today’s interconnected world, the digital landscape is a battlefield. Cyber threats are no longer a distant concern. They are a constant, evolving reality for businesses of all sizes. To navigate this complex environment, organizations need more than just firewalls and antivirus software. They require a robust understanding of their threat landscape. This is where business intelligence (BI) tools for threat analytics become indispensable. These tools transform raw data into actionable insights. They empower security teams to proactively identify, assess, and mitigate risks. This article delves into the crucial role of business intelligence tools for threat analytics. It examines their capabilities, benefits, and the key considerations for selecting the right tools.
The Rising Tide of Cyber Threats
The volume and sophistication of cyber threats are increasing exponentially. From ransomware attacks to data breaches, the potential damage is significant. These threats can cripple operations, damage reputations, and lead to substantial financial losses. Traditional security measures often fall short. They struggle to keep pace with the rapid evolution of attack vectors. This necessitates a shift towards a more proactive and data-driven approach. This is where the power of business intelligence tools for threat analytics comes into play. They provide the necessary visibility and intelligence to stay ahead of the curve.
What are Business Intelligence Tools for Threat Analytics?
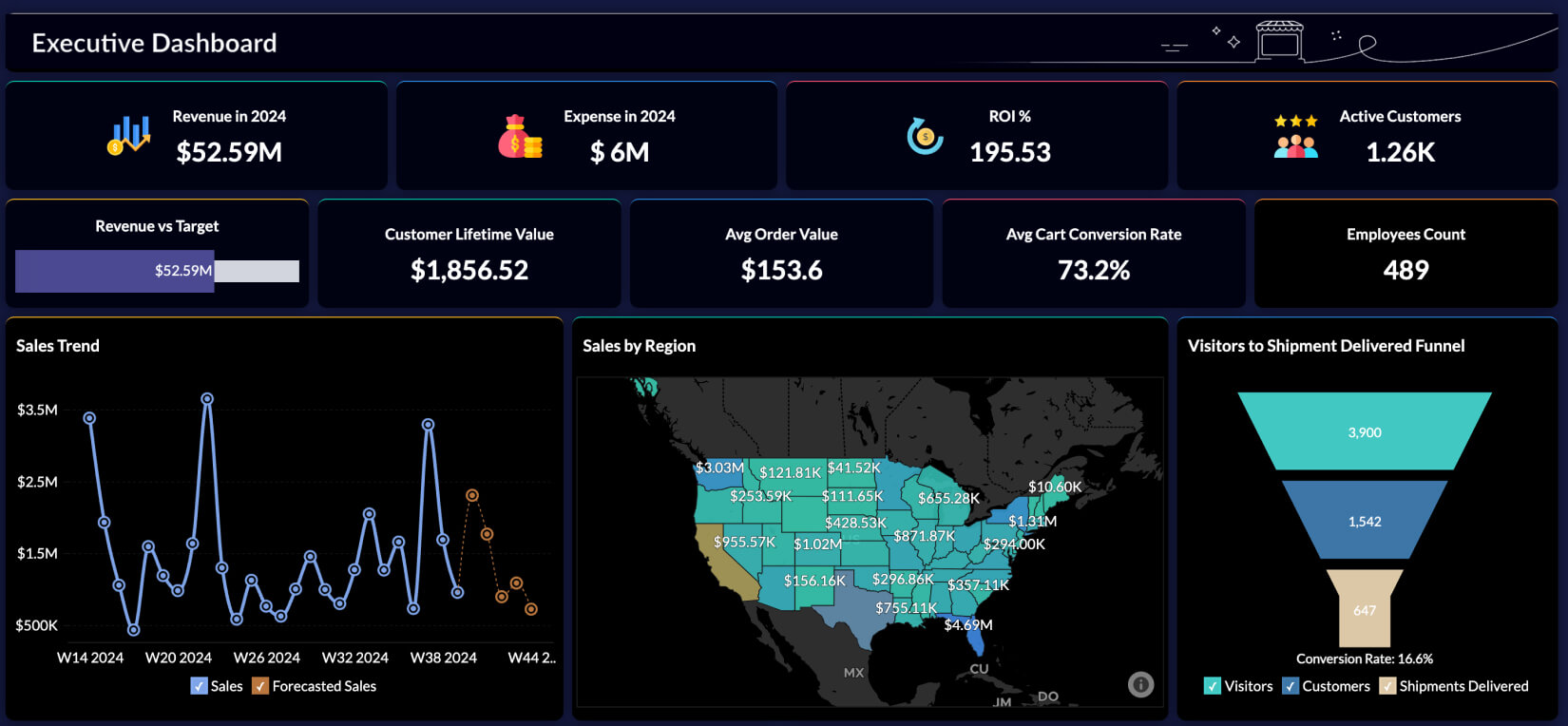
Business intelligence tools for threat analytics are specialized software applications. They are designed to collect, analyze, and visualize security-related data. This data can come from various sources. These include security information and event management (SIEM) systems, intrusion detection systems (IDS), and endpoint detection and response (EDR) solutions. They also integrate with threat intelligence feeds. This integration allows for a comprehensive view of the threat landscape. The core function of these tools is to transform raw security data. It becomes meaningful insights that inform decision-making. They often offer features such as data aggregation, pattern recognition, and predictive analytics. These features enable security teams to identify anomalies, detect threats, and respond effectively.
Key Capabilities of BI Tools for Threat Analytics
Business intelligence tools for threat analytics offer a range of capabilities that are essential for effective threat detection and response. These include:
- Data Collection and Integration: Gathering data from various sources, including logs, alerts, and threat intelligence feeds.
- Data Analysis and Processing: Applying analytics to identify patterns, anomalies, and potential threats.
- Visualization and Reporting: Presenting data in clear, concise dashboards and reports.
- Threat Detection and Alerting: Identifying suspicious activities and generating alerts for security teams.
- Incident Response: Providing tools and information to facilitate incident investigation and remediation.
- Predictive Analytics: Forecasting future threats and vulnerabilities based on historical data.
Benefits of Implementing BI Tools for Threat Analytics
The adoption of business intelligence tools for threat analytics offers numerous benefits to organizations. These benefits translate into improved security posture and reduced risk. These include:
- Enhanced Threat Detection: Early identification of potential threats.
- Improved Incident Response: Faster and more effective responses to security incidents.
- Reduced Risk: Proactive mitigation of vulnerabilities and threats.
- Increased Efficiency: Automation of security tasks and streamlined workflows.
- Better Decision-Making: Data-driven insights to inform security strategies.
- Compliance: Meeting regulatory requirements and industry best practices.
Choosing the Right BI Tools for Threat Analytics
Selecting the right business intelligence tools for threat analytics is a critical decision. It depends on the specific needs and requirements of the organization. Several factors should be considered. These include:
- Scalability: The ability to handle growing data volumes and user demands.
- Integration: Compatibility with existing security infrastructure and data sources.
- Ease of Use: Intuitive interface and user-friendly dashboards.
- Customization: Flexibility to tailor the tools to specific security needs.
- Reporting and Visualization: Robust reporting and visualization capabilities.
- Threat Intelligence Integration: Seamless integration with threat intelligence feeds.
- Vendor Support: Availability of reliable vendor support and training.
- Cost: Total cost of ownership, including licensing, implementation, and maintenance.
Top Business Intelligence Tools for Threat Analytics
Several leading vendors offer business intelligence tools for threat analytics. These tools cater to diverse security needs. Some of the prominent players in this space include:
- Splunk: A leading SIEM platform with robust analytics capabilities.
- IBM QRadar: A comprehensive security intelligence platform.
- LogRhythm: A security intelligence and analytics platform.
- Elastic Security: A platform for security analytics and threat hunting.
- Microsoft Sentinel: A cloud-native SIEM and SOAR solution.
These tools offer a range of features and capabilities. They are designed to address various security challenges. The selection of the best tool depends on the specific needs of the organization. [See also: Choosing the Right SIEM for Your Business]
Implementation Best Practices
Implementing business intelligence tools for threat analytics requires a strategic approach. This ensures successful adoption and optimal results. Some best practices include:
- Define Clear Objectives: Establish specific security goals and objectives.
- Assess Existing Infrastructure: Evaluate current security tools and data sources.
- Plan for Integration: Develop a detailed integration plan.
- Provide Training: Train security teams on the use of the new tools.
- Monitor and Evaluate: Continuously monitor the tools and evaluate their effectiveness.
- Iterate and Improve: Refine the tools and processes based on feedback and results.
The Future of Threat Analytics
The field of threat analytics is constantly evolving. New technologies and approaches are emerging. These are shaping the future of security. Key trends include:
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are playing an increasingly important role in threat detection and response.
- Cloud-Based Security: The adoption of cloud-based security solutions is accelerating.
- Automation: Automation is becoming more prevalent in security tasks.
- Threat Intelligence Sharing: Collaboration and information sharing are essential.
- XDR (Extended Detection and Response): XDR solutions are gaining traction.
These trends will continue to shape the landscape of business intelligence tools for threat analytics. Organizations must stay informed and adapt to these changes. They must do so to remain effective in their security efforts. [See also: The Rise of AI in Cybersecurity]
Conclusion
Business intelligence tools for threat analytics are essential for modern cybersecurity. They empower organizations to proactively manage their threat landscape. By leveraging these tools, businesses can improve their security posture. They can also mitigate risks and protect their valuable assets. Choosing the right tools and implementing them effectively is critical. Organizations must also stay informed about the latest trends and technologies. They must do so to ensure their security efforts remain effective. The digital world demands a proactive and data-driven approach. Business intelligence tools for threat analytics provide the essential foundation for success in this challenging environment.